木馬下載者
Trojan-Downloader.Win32.Agent.d
捕獲時間
2010-3-10
危害等級
高
病毒癥狀
該樣本是使用“VC ”編寫的蠕蟲下載類病毒,由微點主動防御軟件自動捕獲,長度為“249,344字節”,圖標為“
 ”,病毒擴展名為“exe”,主要通過“文件捆綁”、“下載器下載”、“網頁掛馬”、“移動存儲介質”等方式傳播,病毒主要目的為下載安裝木馬程序。
”,病毒擴展名為“exe”,主要通過“文件捆綁”、“下載器下載”、“網頁掛馬”、“移動存儲介質”等方式傳播,病毒主要目的為下載安裝木馬程序。
用戶中毒后,會出現安全軟件無故關閉,網絡運行緩慢,無法進入安全模式,windows系統無故報錯等現象。
感染對象
Windows 2000/Windows XP/Windows 2003/Windows Vista
傳播途徑
網頁掛馬、文件捆綁、下載器下載
防范措施
已安裝使用微點主動防御軟件的用戶,無須任何設置,微點主動防御將自動保護您的系統免受該病毒的入侵和破壞。無論您是否已經升級到最新版本,微點主動防御都能夠有效清除該病毒。如果您沒有將微點主動防御軟件升級到最新版,微點主動防御軟件在發現該病毒后將報警提示您發現“未知后門程序“,請直接選擇刪除處理(如圖1);
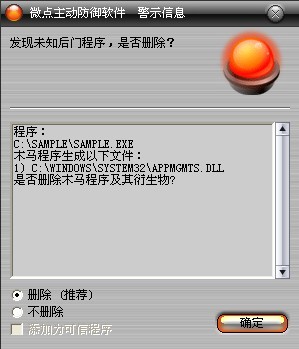
圖1 微點主動防御軟件自動捕獲未知病毒(未升級)
如果您已經將微點主動防御軟件升級到最新版本,微點將報警提示您發現木馬"Trojan-Downloader.Win32.Agent.d”,請直接選擇刪除(如圖2)。
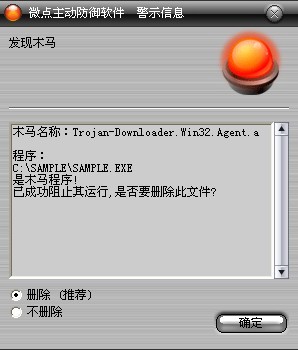
圖2 微點主動防御軟件升級后截獲已知病毒
未安裝微點主動防御軟件的手動解決辦法:
1、手動刪除以下文件:
%Temp%\Forter.sys
%SystemRoot%\system32\X.dll (X為被感染文件名)
2、手動恢復以下注冊表值:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Network
3、用正常系統文件替換%SystemRoot%\system32\X.dll(X為被感染文件名)
4、手動修復被感染rar,htm,html,asp,aspx,exe格式文件
5、手動刪除以下注冊表值:
HKLM\SYSTEM\CURRENTCONTROLSET\SERVICES\FORTER\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\SAFEBOXTRAY.EXE
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\360SE.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\360RP.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\360SD.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\ZHUDONGFANGYU.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\KRNL360SVC.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\360SAFEBOX.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\360SAFE.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\360RPT.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\360HOTFIX.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\修復工具.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\360TRAY.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\360SOFTMGRSVC.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\360SPEEDLD.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\AST.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\VSSERV.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\SECCENTER.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\LIVESRV.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\BDAGENT.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\QUTMSERV.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\360TRAY.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\360SOFTMGRSVC.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\TMPROXY.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\SFCTLCOM.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\TMBMSRV.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\UFSEAGNT.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\AVCENTER.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\AVGUARD.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\SCHED.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\AVGNT.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\AVWEBGRD.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\AVMAILC.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\AVGUARD.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\SCHED.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\MSKSRVER.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\MCSACORE.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\MPFSRV.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\MCVSSHLD.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\MCSYSMON.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\MCSHIELD.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\MCPROXY.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\MCODS.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\MCNASVC.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\MCMSCSVC.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\MCAGENT.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\CCSVCHST.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\CCSVCHST.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\CCSVCHST.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\EKRN.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\EGUI.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\KMAILMON.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\KWATCH.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\KSWEBSHIELD.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\KPFWSVC.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\KPFW32.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\KISSVC.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\KAVSTART.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\CCENTER.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\SCANFRM.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\RSTRAY.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\RSNETSVR.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\RSAGENT.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\RAVTASK.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\RAVMOND.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\AVP.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\AVP.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\AVP.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\KVSRVXP.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\KVMONXP.KXP
變量聲明:
%SystemDriver% 系統所在分區,通常為“C:\”
%SystemRoot% WINDODWS所在目錄,通常為“C:\Windows”
%Documents and Settings% 用戶文檔目錄,通常為“C:\Documents and Settings”
%Temp% 臨時文件夾,通常為“C:\Documents and Settings\當前用戶名稱\Local Settings\Temp”
%ProgramFiles% 系統程序默認安裝目錄,通常為:“C:\ProgramFiles”
病毒分析
(1)比較自身是否作為服務運行,如果不是則試圖打開管道“96DBA249-E88E-4c47-98DC-E18E6E3E3E5A”執行命令。并遍歷svchost.exe進程的服務項,判斷服務是否正在使用,如果有沒有使用的服務則讀取該服務的dll文件,加載sfc_os.dll以去除Windows文件保護。將自身數據全部寫入該DLL中,創建文件%SystemDriver%\Delinfo.bin記錄自身路徑等信息,開啟該服務,將被感染的服務文件載入運行。退出主進程。
(2)如果自身是作為服務運行則創建線程,讀取delinfo.bin中的信息,刪除病毒源文件并刪除Delinfo.bin。遍歷進程,如果發現kav.exe或bdagent.exe則運行相關代碼試圖躲避殺毒軟件查殺。并始終檢自身運行狀態,監視安全軟件運行狀態,解密出自身數據。釋放驅動程序%Temp%\Forter.sys 并創建名為“Forter”的服務加載驅動程序,執行成功后刪除驅動文件以及鍵值
(3)與驅動交互,計算內核態函數地址,計算SSDT地址并恢復SSDT,將自身啟動信息發送給驅動創建注冊表啟動,創建注冊表劫持大量安全軟件。遍歷進程,查找大量殺毒軟件進程,如果找到則傳入驅動,關閉安全軟件進程。
(4)創建線程,從指定網址下載病毒木馬運行,創建管道“\\.\pipe\96DBA249-E88E-4c47-98DC-E18E6E3E3E5A”,聽取命令。
(5)刪除安全模式相關注冊表鍵值,破壞安全模式。
(6)清除Host,創建線程,搜索并感染文件rar,htm,html,asp,aspx,exe格式文件。
(7)感染移動介質,移動介質中創建autorun.inf以及“recycle.{645FF040-5081-101B-9F08-00AA002F954E}\Setup.exe”
(8)查找局域網計算機,并嘗試弱口令攻擊,如果入侵成功,則在C盤釋放CONFIG.exe,并使用at命令計劃執行病毒文件。
病毒創建文件:
%Temp%\Forter.sys
%SystemRoot%\system32\X.dll (X為被感染文件名)
病毒刪除文件:
%Temp%\Forter.sys
病毒創建注冊表:
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\SAFEBOXTRAY.EXE
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\360SE.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\360RP.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\360SD.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\ZHUDONGFANGYU.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\KRNL360SVC.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\360SAFEBOX.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\360SAFE.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\360RPT.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\360HOTFIX.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\修復工具.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\360TRAY.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\360SOFTMGRSVC.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\360SPEEDLD.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\AST.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\VSSERV.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\SECCENTER.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\LIVESRV.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\BDAGENT.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\QUTMSERV.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\360TRAY.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\360SOFTMGRSVC.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\TMPROXY.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\SFCTLCOM.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\TMBMSRV.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\UFSEAGNT.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\AVCENTER.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\AVGUARD.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\SCHED.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\AVGNT.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\AVWEBGRD.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\AVMAILC.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\AVGUARD.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\SCHED.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\MSKSRVER.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\MCSACORE.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\MPFSRV.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\MCVSSHLD.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\MCSYSMON.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\MCSHIELD.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\MCPROXY.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\MCODS.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\MCNASVC.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\MCMSCSVC.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\MCAGENT.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\CCSVCHST.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\CCSVCHST.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\CCSVCHST.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\EKRN.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\EGUI.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\KMAILMON.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\KWATCH.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\KSWEBSHIELD.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\KPFWSVC.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\KPFW32.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\KISSVC.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\KAVSTART.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\CCENTER.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\SCANFRM.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\RSTRAY.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\RSNETSVR.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\RSAGENT.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\RAVTASK.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\RAVMOND.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\AVP.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\AVP.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\AVP.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\KVSRVXP.EXE\
HKLM\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\IMAGE FILE EXECUTION OPTIONS\KVMONXP.KXP
病毒刪除注冊表:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Minimal
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Network
病毒訪問網絡:
http://a.nb***01.com:6969/announce
http://b.nb***01.com:6969/announce
http://c.nb***01.com:6969/announce
http://d.nb***01.com:6969/announce
http://e.nb***01.com:6969/announce
http://f.nb***01.com:6969/announce
http://g.nb***01.com:6969/announce
http://up.nb***01.com/Down/33.rar
